As a leader in the digital age, you are applying new technologies and embracing robotic process automation, 5G, internet of things (IoT), cognitive capabilities and artificial intelligence (AI), cloud computing, predictive analytics and blockchain to rapidly impact the way you:
- Reach and service your target markets.
- Service and deliver value in your products and services.
- Create personalised experiences.
Powered by the recent global pandemic events, digital transformation journeys accelerated across all industries.
Staff need remote access to their files and applications. Customers want to order products using online shopping. To these needs, organisations accelerated the migration of their solutions for:
- Productivity and workplace innovation to systems like Microsoft 365, Google Suite and Apple iWork.
- Backoffice to Amazon Web Services, Google Cloud or Microsoft Azure.
- Collaboration to Zoom, Miro, Wrike, Smarsheets etc.
While these off-the-shelf solutions and SaaS services separately meet several of their needs, they are still fundamentally stand alone. They may not necessarily tend to the specific needs of the workflows of your organisation. In these cases, businesses engage in tailor-made/custom/bespoke software development to:
- Modernise legacy applications that cannot be migrated using like-for-like 'lift and shift' practices.
- Support line-of-business workflows.
- Integrate different solutions from separate providers through published APIs.
- Meet unique privacy or security requirements.
- Replace and consolidate legacy solutions
For you, this means that now you have to deal with managing Cyber and Technology risk across:
- Suppliers of solutions to businesses globally (e.g. Microsoft, Amazon, Apple, Google etc.).
- Suppliers of services to enable you to conduct your core business purpose.
- Custom solutions that are built to your specifications and measures.
This means that any discussion around understanding and managing the risk of Cyber and Technology spans:
- Your existing IT & future-IT infrastructure landscape.
- Any solutions being developed or under consideration to be developed (in-house or outsourced).
- Any merger & acquisitions that the business may be doing or considerating, as you will need to consolidate your risk management across the combined company (and within what timeframes).
This is not a small task!
Assessing your digital exposure to cyber & technology risk
Now that we are post-pandemic and have achieved a minimum sense of distributed operational resilience, we need to manage the Cyber and Technology risks of our digital innovations.
Research from Purplesec indicates that
- Cybercrime grew 600% in 2020/2021.
- 43% of cyber-attacks target small businesses, of which 70% are not equipped to deal with such attacks.
- 48% of data security breaches are caused by acts of malicious intent. Human error or system failure account for the rest.
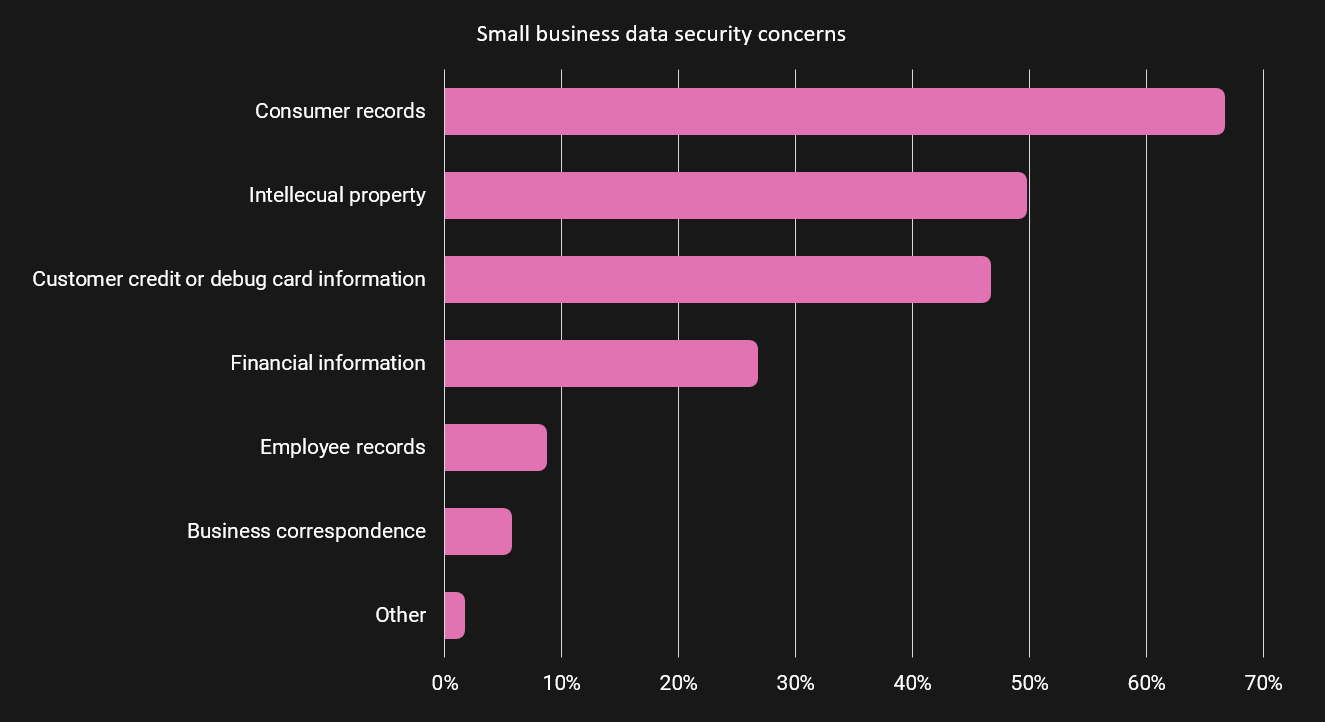
Powered by increasing network capabilities with higher speeds, high-compute performance, real-time operations, and wireless connectivity, we see a skyrocketing trend in:
- Ransomware attacks (data-encrypting programs that demand payment to release the infected data back to you).
- Ransomware as a Service (RaaS) operators (revenue-generating organisations via monthly membership fees, affiliate programs, licensing fees, profit sharing models and more).
- Swift exploitation major disasters.
- Impersonation of official websites and domains (delivery, pandemic).
- Targeted attacks (e.g. delivery scams, boosted by the rise of eCommerce and work from home).
- Digital hygiene weakness (individual complacency or devices used for personal browsing and gaming that may not have been vetted for IT policy compliance).
- New, more sophisticated, intelligent and bolder attack methodologies.
- Cyberattacks against the state, healthcare, finance, and industrial control structures.
"Security leaders must demonstrate to the C-Suite and the bord not only that they understand the criticality of the continuity of operations, but also the importance of working in partnership with the whole business to manage risk effectively", Howard Marshall, Managing Director, Accenture Security.
Attack Vectors

Attack vectors remain focused around:
- Social engineering, Phishing (email-based) and Sphishing (SMS-based) messages designed to trick recipients.
- Stolen credentials.
- Targeted infection against an endpoint that is using slightly outdated software.
- Scareware and other blackmailing techniques directed towards manipulating humans to attain specific goals.
Attackers are increasingly impersonating executives within organisations. Using an example, they pose as the Center for Disease Control and Prevention (CDC) or World Health Organisation (WHO) to deliver digital packages designed to deceive and trick users into clicking links and opening attachments containing malware and other types of trouble.
Studies confirm that email remains the top vector for communication, accounting for around 80% of incidents. The results observed that you only need one employee to take the bait and compromise your company.
7% of employees fall for phishing attacks and over 60% fall for spear phishing.
Research from Graphus and PtSecurity, reports that:
- 77% - Attacks are targeted
- 99.7% - of documents used in attachment-based malware campaigns rely on social engineering (e.g. masking as fake bills, invoices, legal notices, delivery notices etc.)
- 65% - of social engineering attacks are successful
- 70% - Of consumers would consider leaving a retailer that falls victim to a ransomware attack
What does this mean for you?
As a digital leader, it is your responsibility to understand that the older ways a business has accounted for these risks may not work anymore or are too cumbersome to scale today.
You need to establish a comprehensive framework that enables the proper management of the digital dimension of your business to:
- Keep pace with the expanding digital footprint to do work.
- Balance and manage the costs and risks of cyber threats to your environments and productivity.
- Develop and maintain security policies.
- Enable people to work from any device or location of choice securely while keeping up with modern security demands.
The bottom line is that you are and remain responsible for managing your business's Cyber and Technology risk.
Typical security layers to achieve due diligence practices:
- Backup & Disaster Recovery
- Endpoint Protection (e.g. Firewall, USB control, AV & Malware protection)
- File integrity management & access control
- Patch Management
- Mail, Chat and Web Protection & Content Filtering
- Intrusion Detection, Security Information and Event Management
- Risk intelligence
- Password management
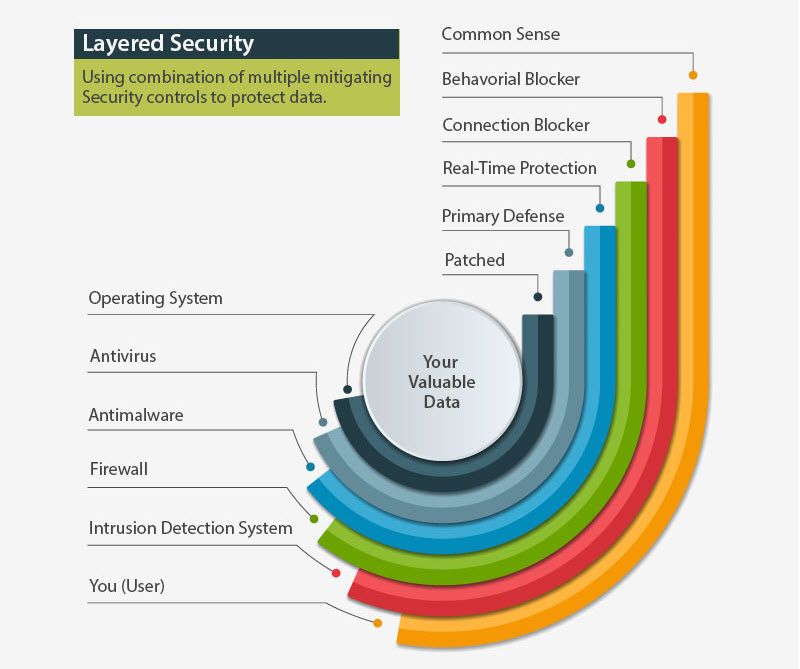
If you are also providing services as a cloud service provider or online solution, you are also responsible for protecting the infrastructure and the data used to deliver your services. In this regard, you need to pay strong attention to how your cloud storage is configured, the security of your APIs and the actions your end-users can perform on your services.
To mitigate, one needs to Deploy mechanisms and practices to
- Deploy instrumentation to identify and set a baseline on what normal looks like.
- Actively monitor for vulnerabilities in the configurations and software setups of their own infrastructure.
- Deploy security layers to monitor, manage and secure your digital footprint.
- Upgrade your tooling to minimise reliance on the machine's configuration from which users are doing their work.
- Develop cybersecurity expertise (developing it in-house or use the services offered by MSSPs to stay focused on core purpose).
- Detect and report the rate of attacks that were mitigated.
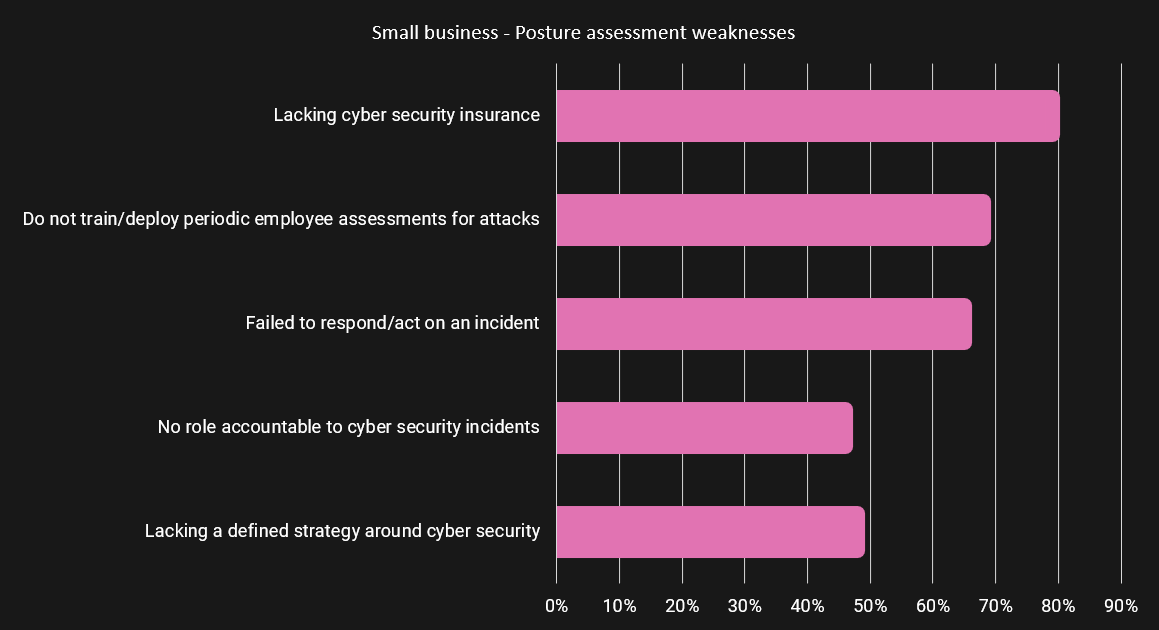
The sudden shift of massive volumes of people to embrace remote working drove impressive pressures on traditional IT organisations. They went from a progressive direction towards enabling remote work to full-scale activated mode. This rapid shift focused on helping continued productivity and retention of customer services. It surely has left various unsecured gaps that malicious attackers can use to exploit for their financial gain.
Let's make no mistake. The changes that shaped the workforce in 2020/2021 are here to stay. Cybercrime will stay too, and with such an increasing reliance on technology, we can expect to see modernised attacks in increasing scale, boldness and sophistication.
IT departments will need to restructure and continue investing in developing:
- Internal DevOps capabilities to automate whatever possible.
- Policies and quality standards that are deployed, met and enforced within the workforce.
- Train stakeholders to respond to them.
Reporting the value of the investment
Your organisation needs to value the work you are doing and know with confidence that the investment they authorised is paying off.
You need to ensure your tooling enables you to select meaningful metrics to show off the benefits of what was implemented. Some examples:
- Number of attacks detected and diffused.
- Number of vulnerabilities detected and addressed within a key timeframe (with examples of impact to companies that did not react with equal velocity).
- Impact on productivity & efficiencies (proxy measured by the count of cases opened with IT related to infected machines).
- Transparency of activities of interest to lead to better manage risk etc. (e.g. users logging on to services from locations outside of the country they reside).
- Reduced hours on break/fix activities within IT.
- % of issues remedied.
Wrapping up!
Digital Transformation journeys are exciting and unlock several value-doors for organisations. They also bring with them new Cyber and Technology risks to be understood and managed. As a digital leader, you hold the baton to:
- Bring different stakeholders on board.
- Align business requirements to solutions.
- Equip talent and suppliers with knowledge and tooling.
- Deploy ongoing training capabilities.
- Communicate frequently to engage and align stakeholders continually.
Managing the risk of Cyber & Technology requires ongoing vigilance across:
- Infrastructure
- Access controls
- Third-party productivity solutions
- Software development practices (in-sourced / outsourced)
- Behaviours (at the edge and within your organisation)
We can easily imagine your digital ecosystem as a human body. As much as our bodies are sophisticated in their defences, they still tend to get periodic colds and flu attacks. It is not even a matter of whether we will get a cold or flu but when. The same holds for cyber attacks.
Like a nasty cold and flu, we will continue seeing mutations and new trends in cyber attacks and technology risks. As a result, we need to continually improve and be proactive at anticipating and stopping these evolutions.







